JIT and Azure AD: Sending Groups via SAML Attributes
Overview
In this article you learn how to transmit groups from Azure AD during Just In Time Provisioning.
Since Azure AD only supports sending group ids instead of group names, you also have to create a group transformation for each group.
Please note that there is a limit in Azure AD for only 150 groups to be sent as values in the attribute in the SAML response. If the number of groups the user is in goes over that limit (150 for SAML) then an overage claim will be added to the claim sources pointing at the Graph endpoint containing the list of groups for the user, which cannot be processed by the plugin in JIT.
Configure Azure AD for Transmitting Groups via SAML Attributes
With its default settings, Azure AD does not send group ids for Just In Time Provisioning.
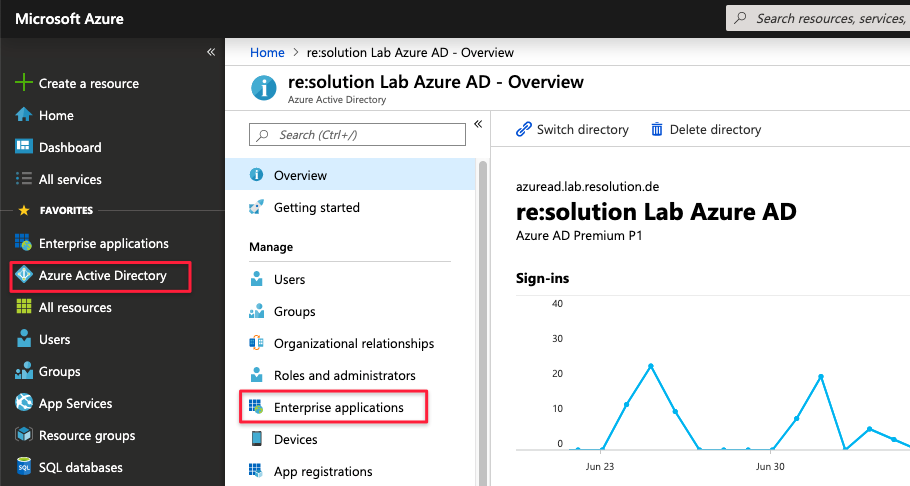
To change this, navigate to the Enterprise Application you've created for your Atlassian instance in Azure AD:
Click on Azure Active Directory in the left panel and then click on Enterprise applications
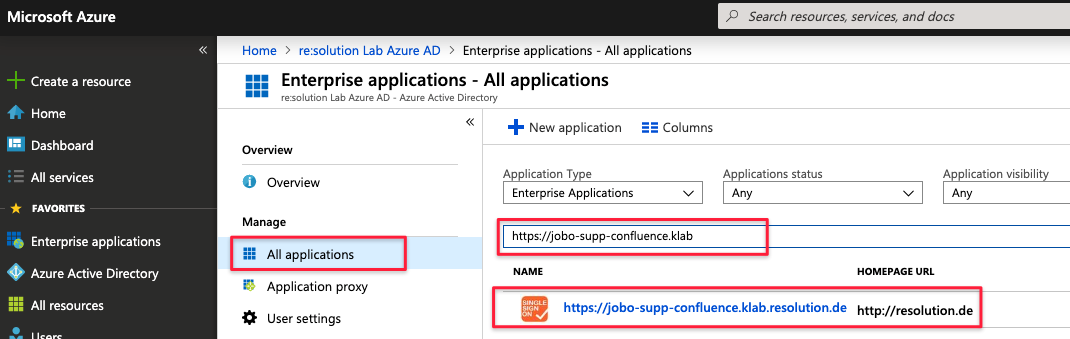
Next, click on All Applications and search for the Enterprise Application you have created for the SAML SSO app and click on its name:
Once opened, click on Single sign-on and then then the pencil icon beside User Attributes & Claims
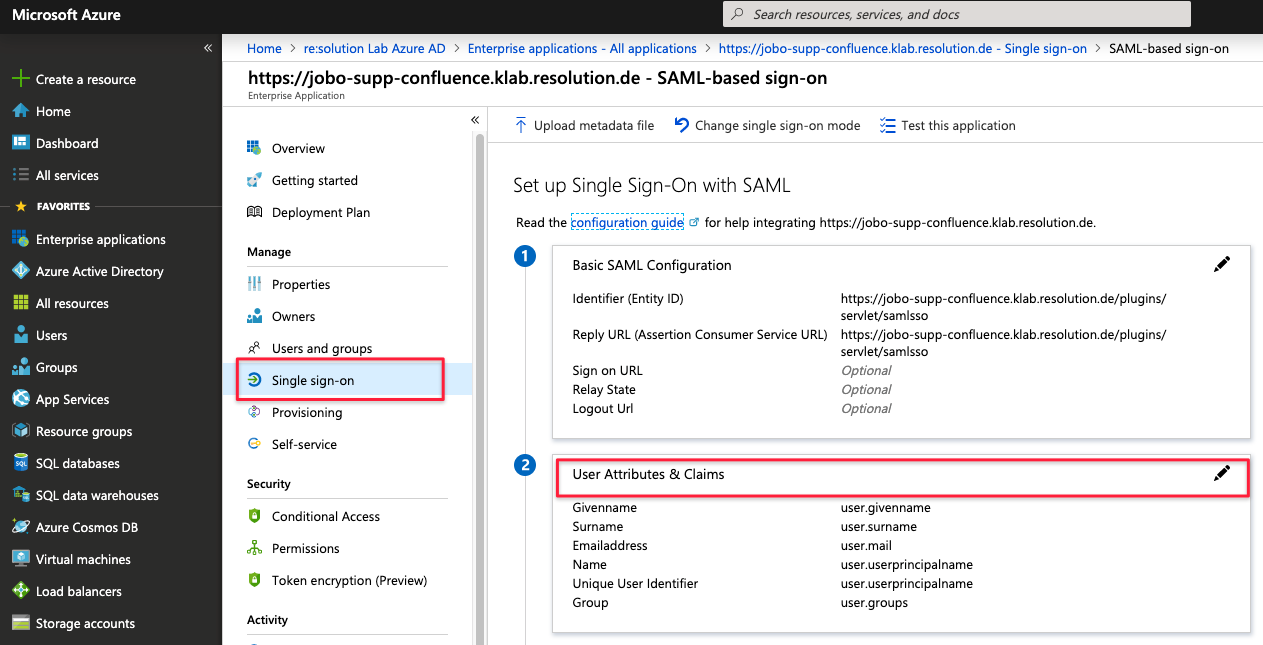
Click on the pencil icon beside Groups returned in claim
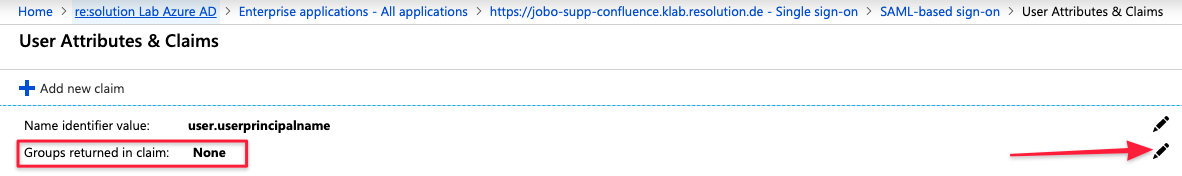
and change the settings to All groups and save your settings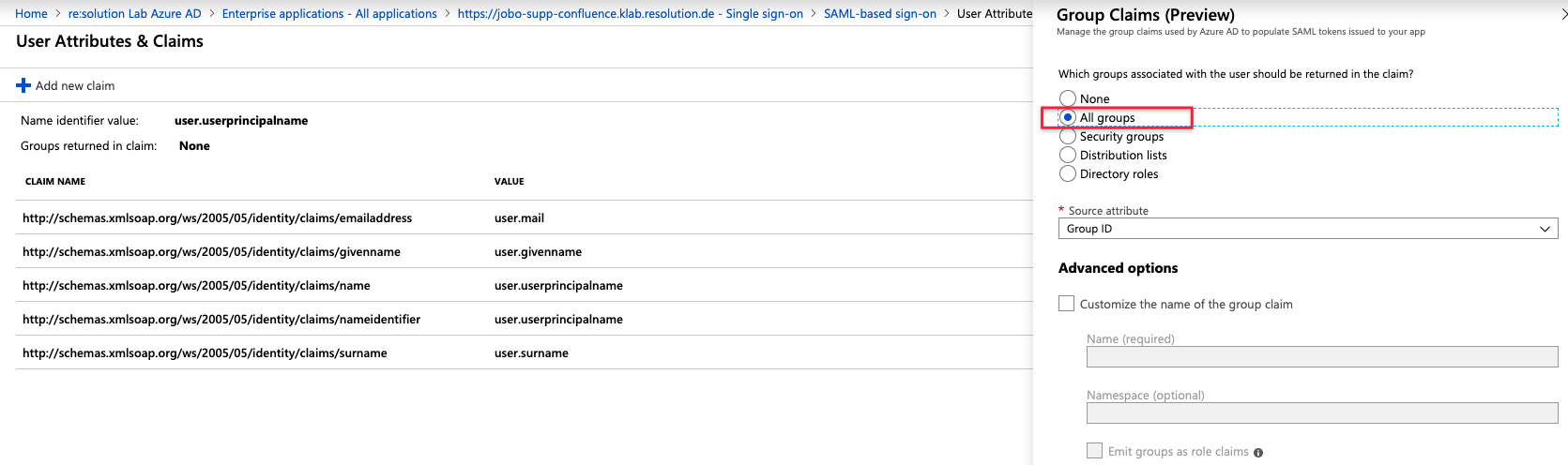
Now, Azure AD will send the group ids of a user when logging in.
These you need to convert into the human readable name by using group transformation rules for each.
This is described in the next chapter as part if the SAML SSO app configuration.
Configure the SAML SSO app for JIT with Azure AD
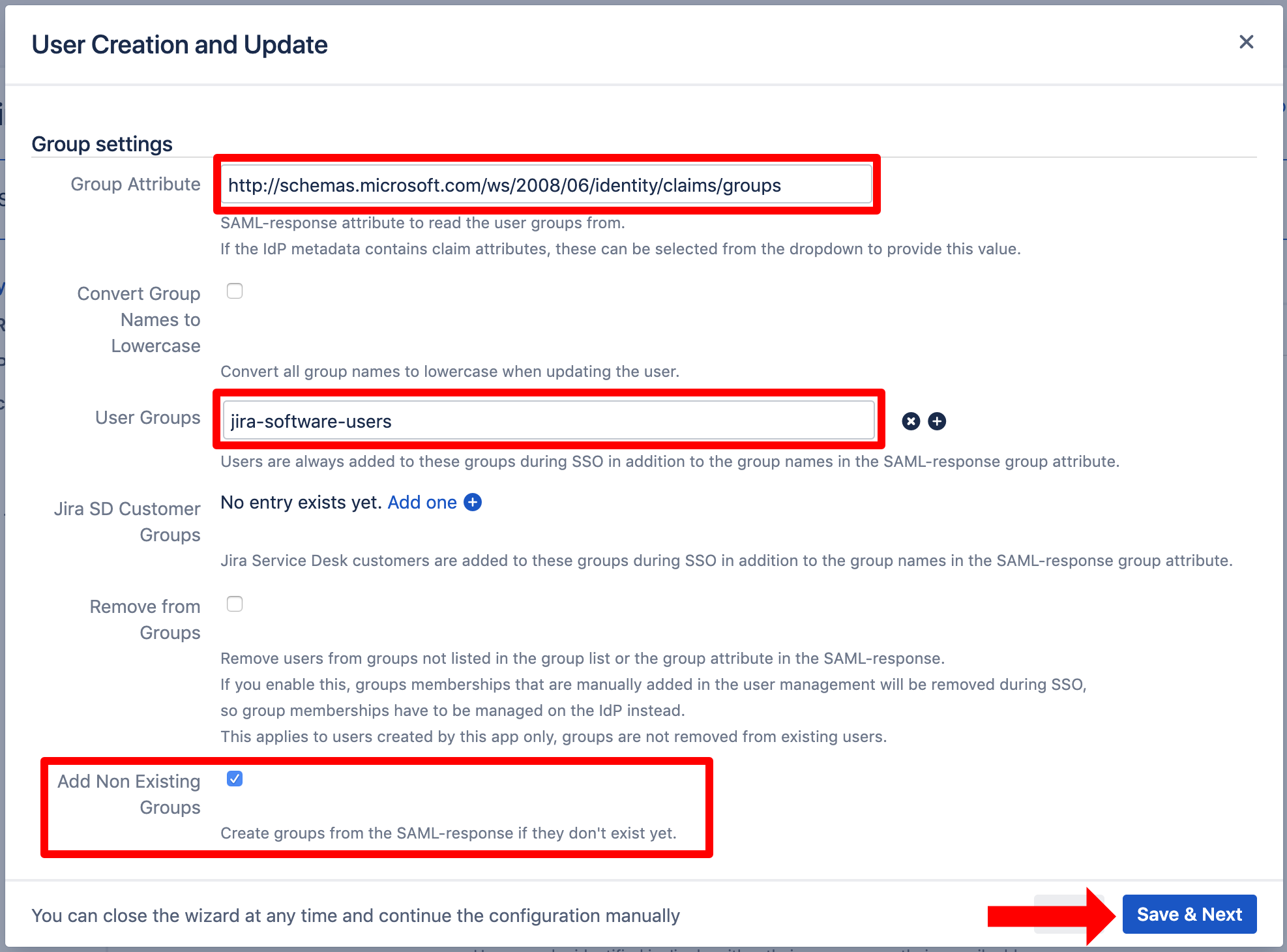
Now, scroll down in the Wizard to access the group settings. For the "Group Attribute", use "http://schemas.microsoft.com/ws/2008/06/identity/claims/groups".
Depending on your Atlassian product, it is a good idea to set (default) user group(s) for new users, such as "jira-software-users" for Jira or "confluence-users" for Confluence.
Without assigning new users to the product specific group, they are not able to use your Atlassian product. Also, feel free to activate any option which suits your needs.
To create groups automatically which do not exist in your Atlassian product, activate "Add Non Existing Groups".
Click "Save & Next" to continue.
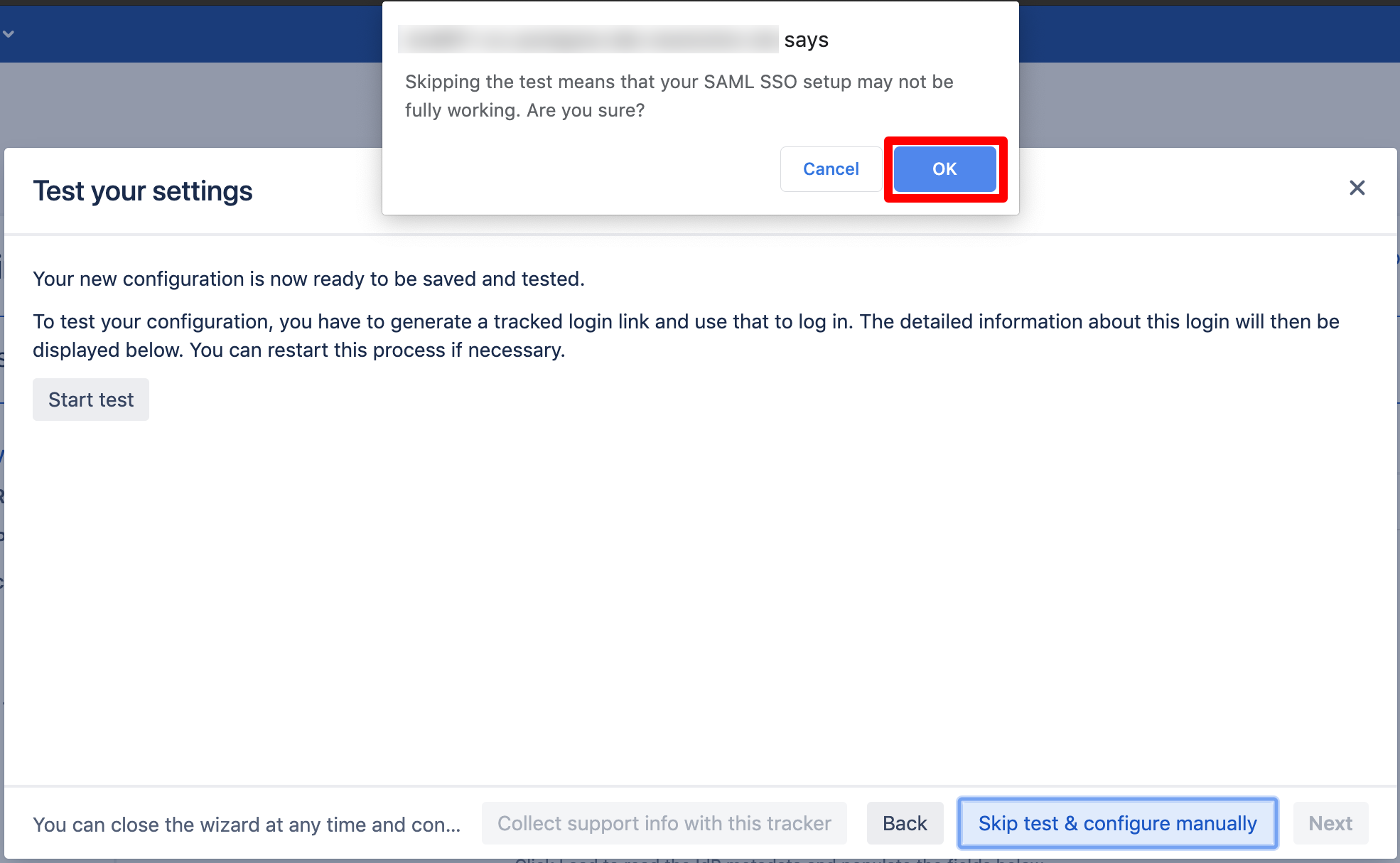
Click "Skip test & configure manually".
Click "OK". Now, the wizard will be closed and you can see the full configuration the SAML SSO app.
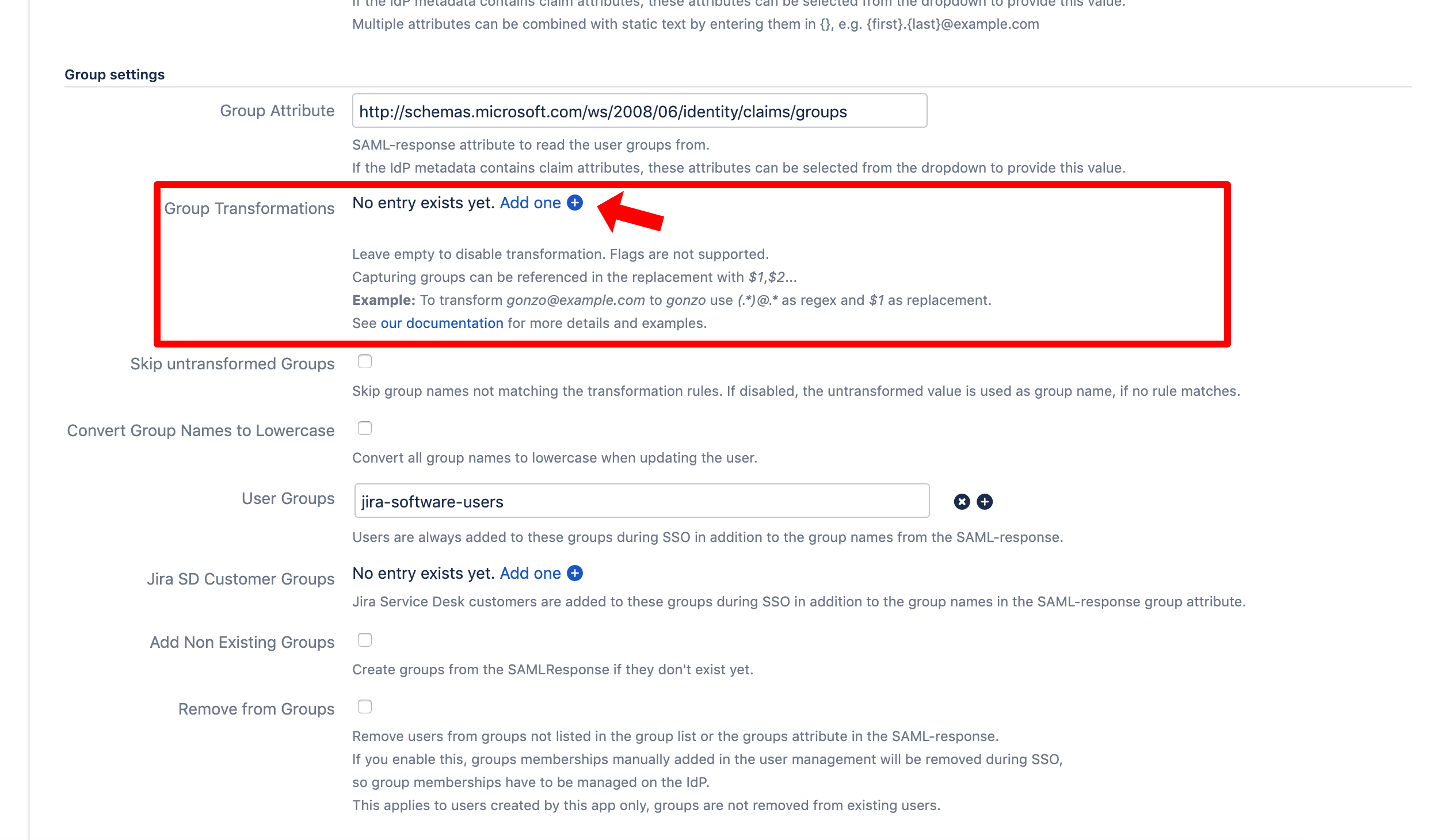
Scroll down in the configuration to "Group settings".
Since Azure AD only transfers group ids and not group names, group transformations must be created for each group Id.
Click on "Add one" to add a new group transformation.
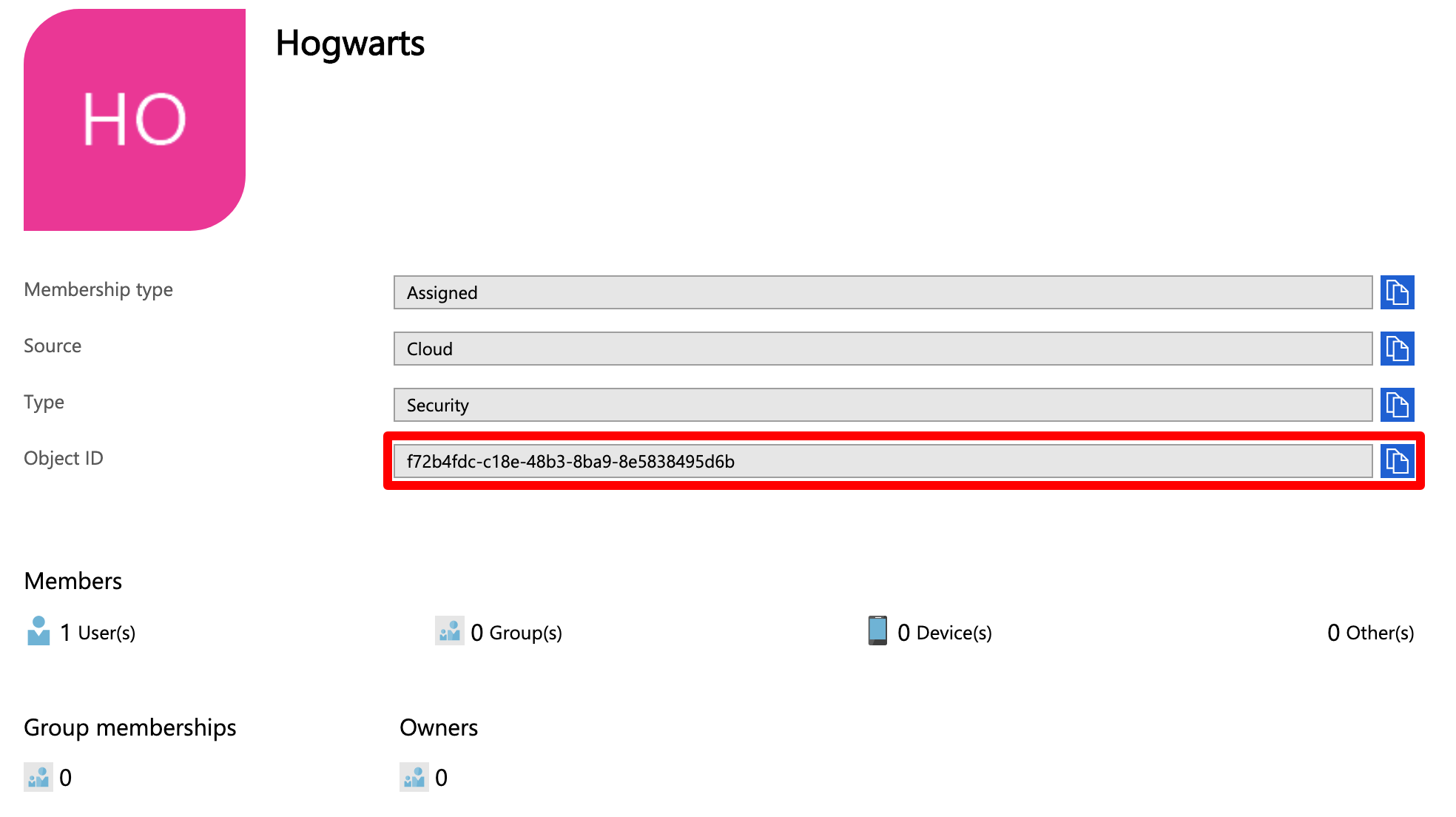
To create a transformation for a group id to a name, you need the group id.
The id of a group can be found in Azure AD on the page of the group. Copy the Object ID.
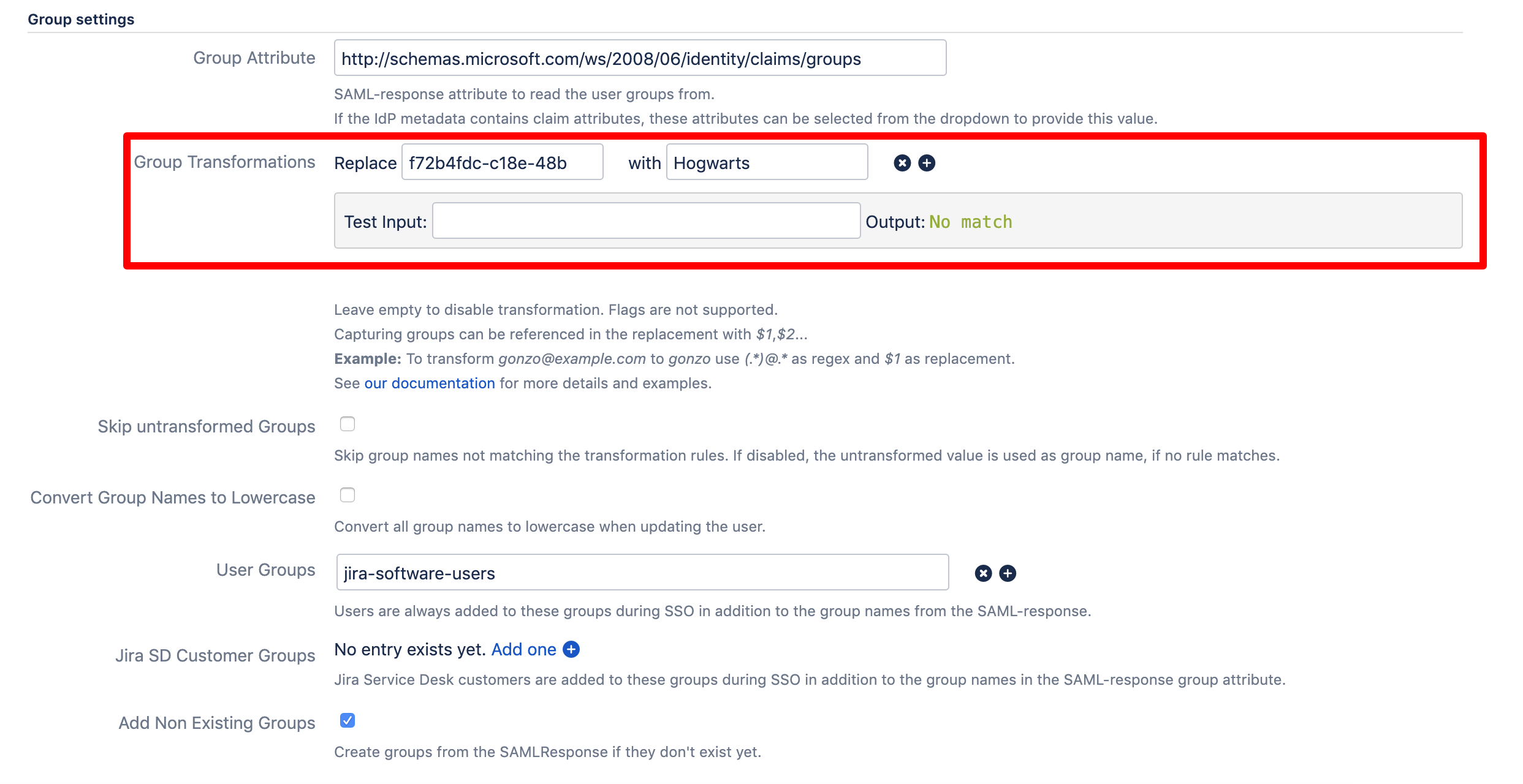
Back in your Atlassian product, paste the Object ID into the textfield next to "Replace" and the group name into the textfield next to "with".
Now, when Azure sends the group ID, it will be automatically transformed to the the specified group.
If you want to transform multiple group ids, press the plus button to add more transformations.
Now scroll up to the beginning of the page and click "Save settings".