Azure AD B2C with Just-In-Time Provisioning
After completing this setup guide, you will set up Azure AD B2C with Just-In-Time Provisioning and your Atlassian product for the SAML SSO app. Additionally, you will enable the SSO redirection and test SSO.
Azure AD B2C only supports transmitting group ids via SAML attributes, not the group names. This tutorial assumes that you manage your groups locally and not with Azure AD B2C. If you like to manage groups via Azure AD B2X and using JIT, you have to edit the manifest of the Azure enterprise application and create a transformation rule per group, which transforms the group id to a name. Please have a look at our KB for further information.
Prerequisites
To use the SAML SSO app with Azure AD B2C, you need the following:
An Azure AD subscription
An Azure AD B2C Tenant (please check this Microsoft article for more information)
A (trial) subscription for the SAML SSO app
Admin access to your Atlassian product
Step-By-Step Setup Guide
Install the SAML SSO app
In your Atlassian product, open the in-product marketplace as described in the Atlassian documentation.
Search for "resolution saml" and click "Install" for SAML Single Sign On (SSO) by resolution Reichert Network Solutions GmbH.
After the installation is complete, click Manage Apps/Addons.
Configure SAML SSO
For the next steps, please go to Manage apps (or addons), choose SAML SSO and click Configure.
First Steps - Wizard
After you click "Configure", the Wizard will be triggered. If not, or if you want to add another Identity Prover (IdP) to your existing configuration, click on "+ Add IdP". This guide assumes, that there is no IdP configured.
The Wizard greets you with information, click on "Add new IdP" to proceed.For the IdP Type, choose "Azure AD". You can also choose a name. Click on "Next" to continue.
In the next step, you will configure Azure AD B2C. Please keep this tab open or copy the information.
Create and Configure an Azure Enterprise App for SAML SSO
Adding an Enterprise Application for the SAML SSO App
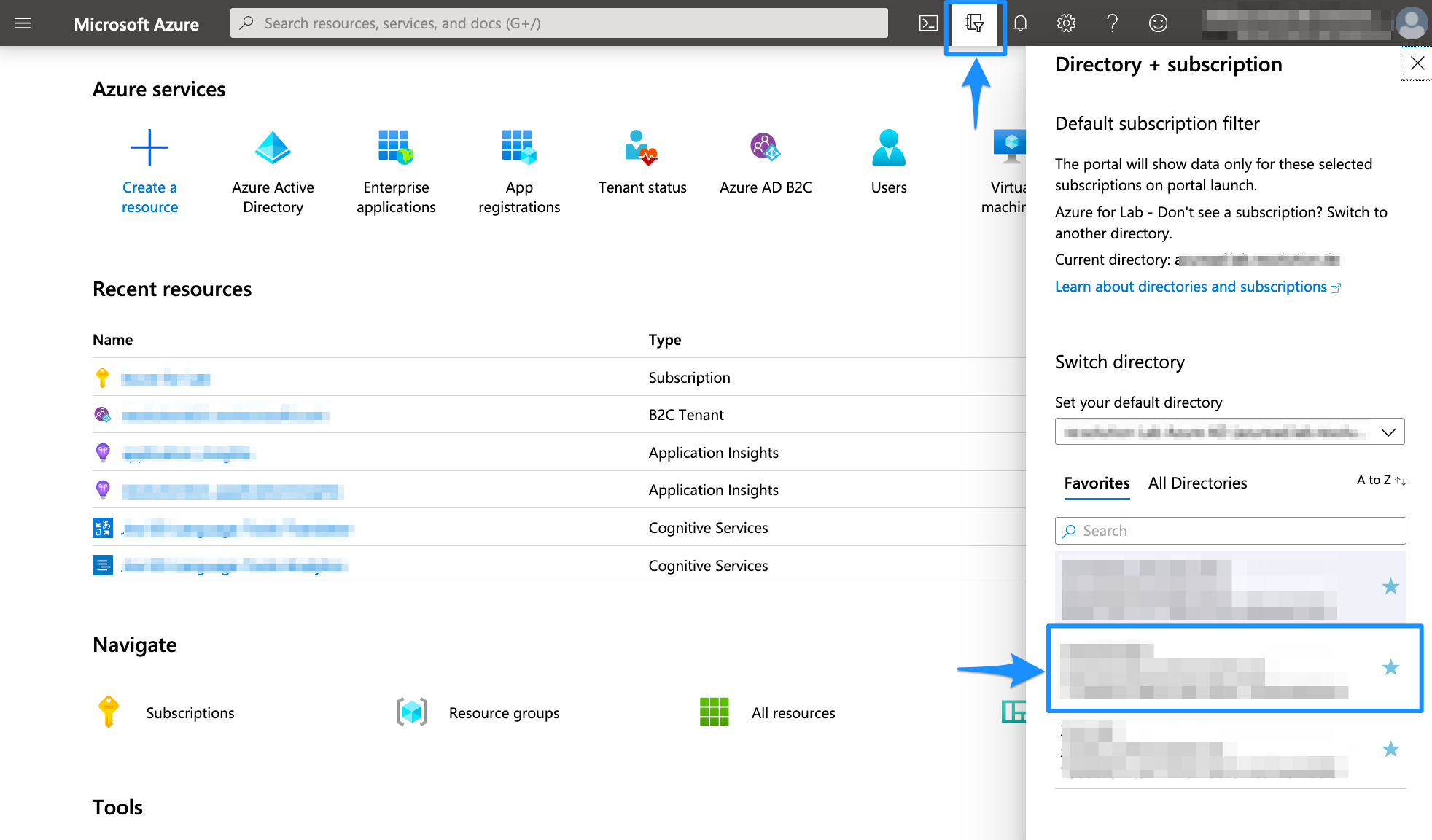
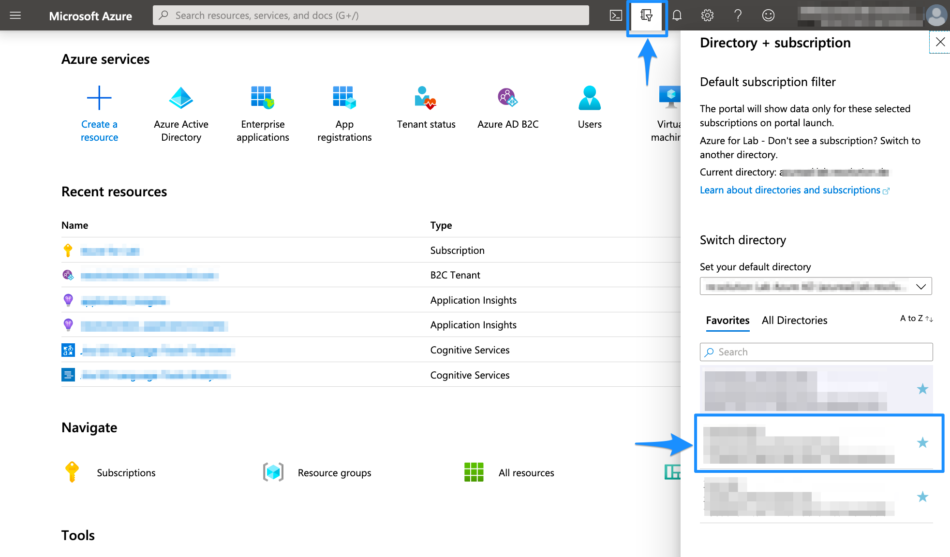
Navigate to http://portal.azure.com.
Select the Directory + Subscription icon in the portal toolbar, and make sure you have selected the directory that contains your Azure AD B2C tenant.
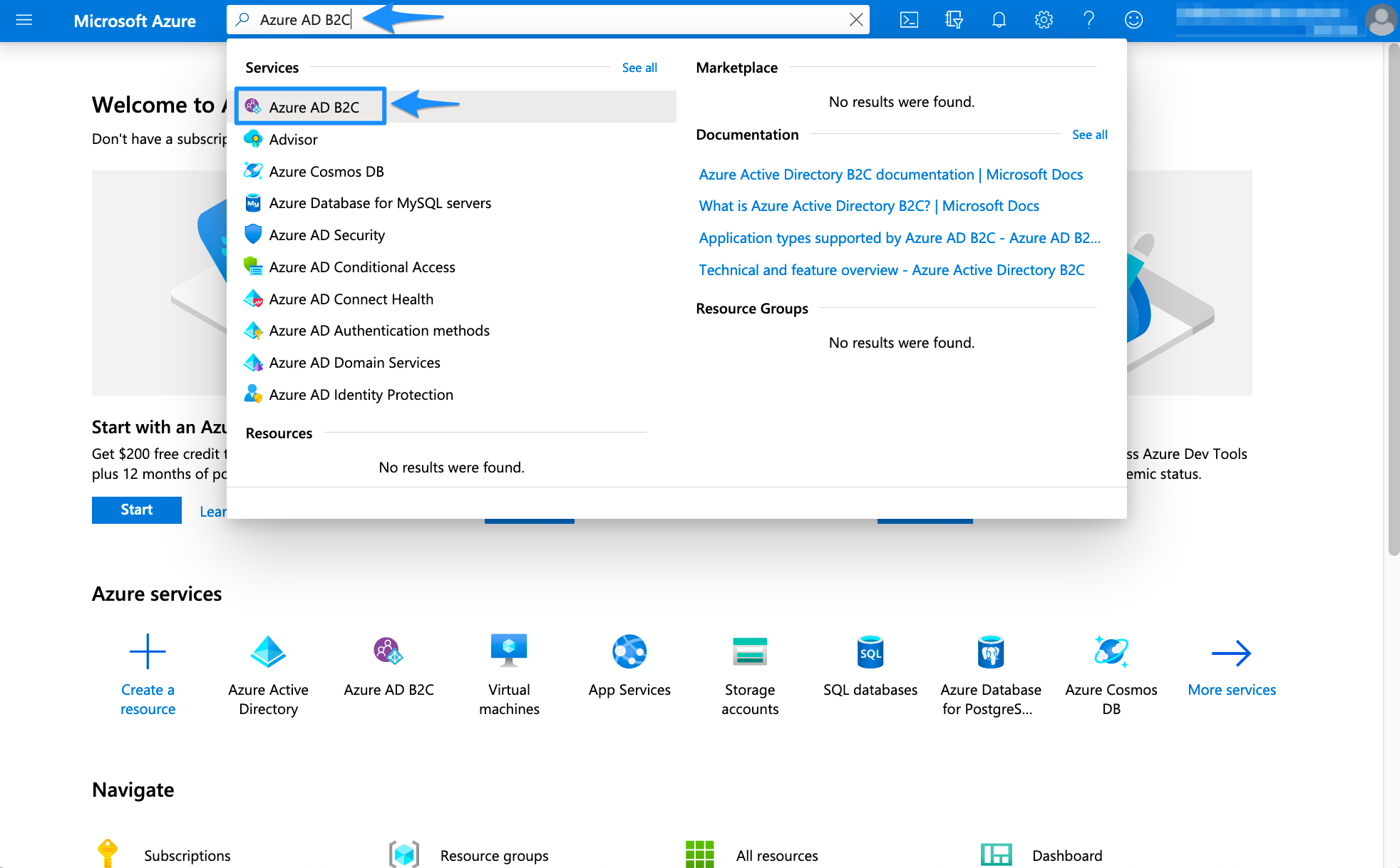
In the Azure portal, search for and select Azure AD B2C.
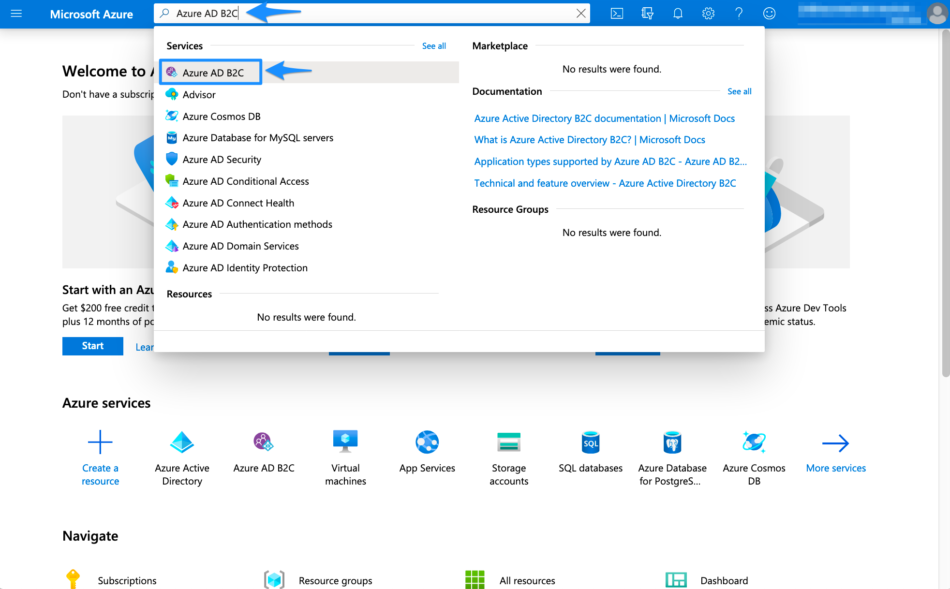
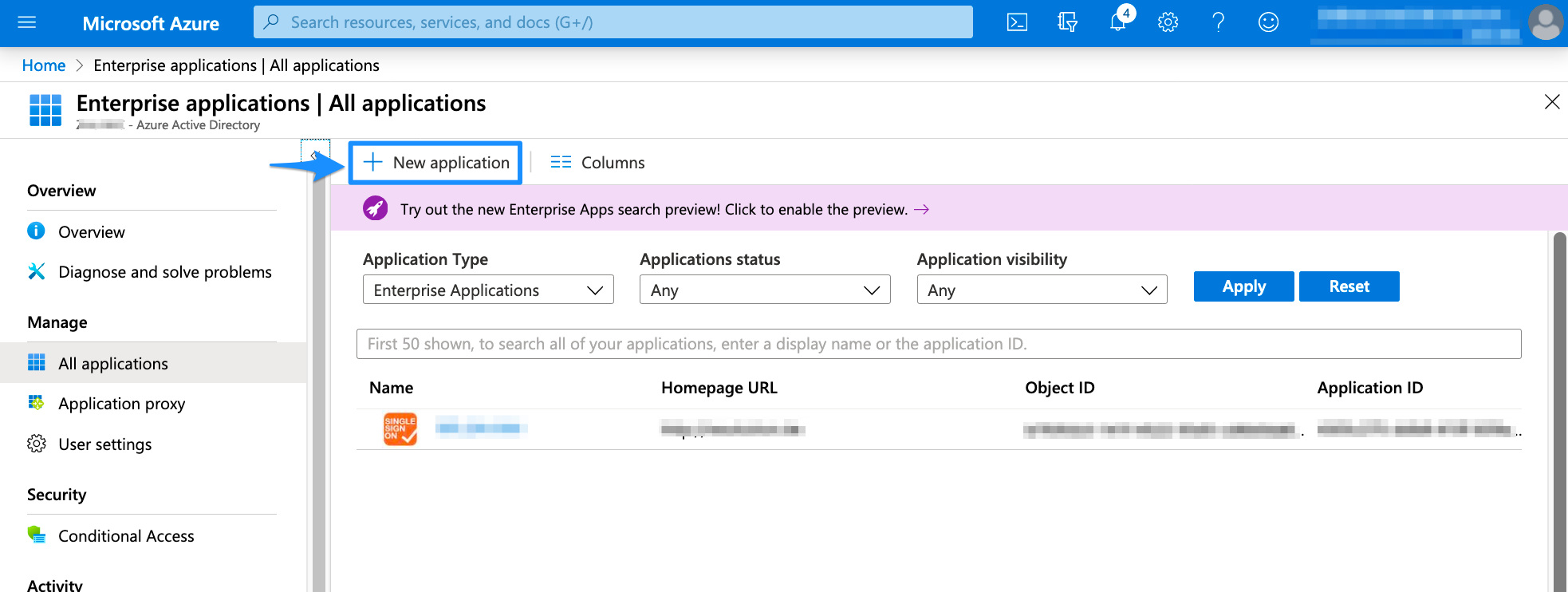
Navigate to the Azure Active Directory page, then select Enterprise applications under Manage in the left panel.
Select New Application to add a new enterprise application.
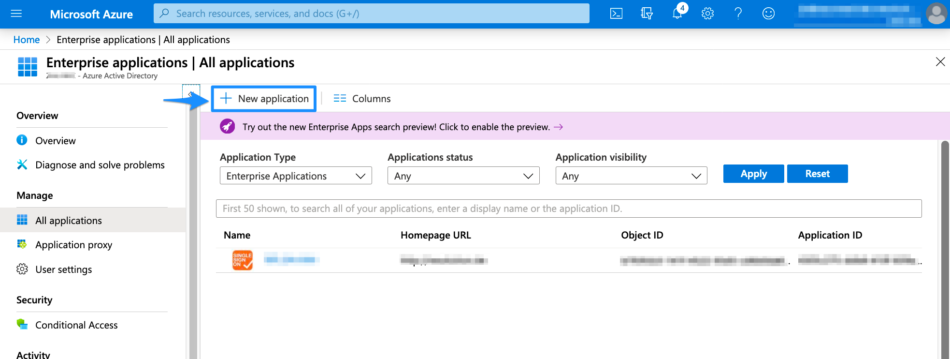
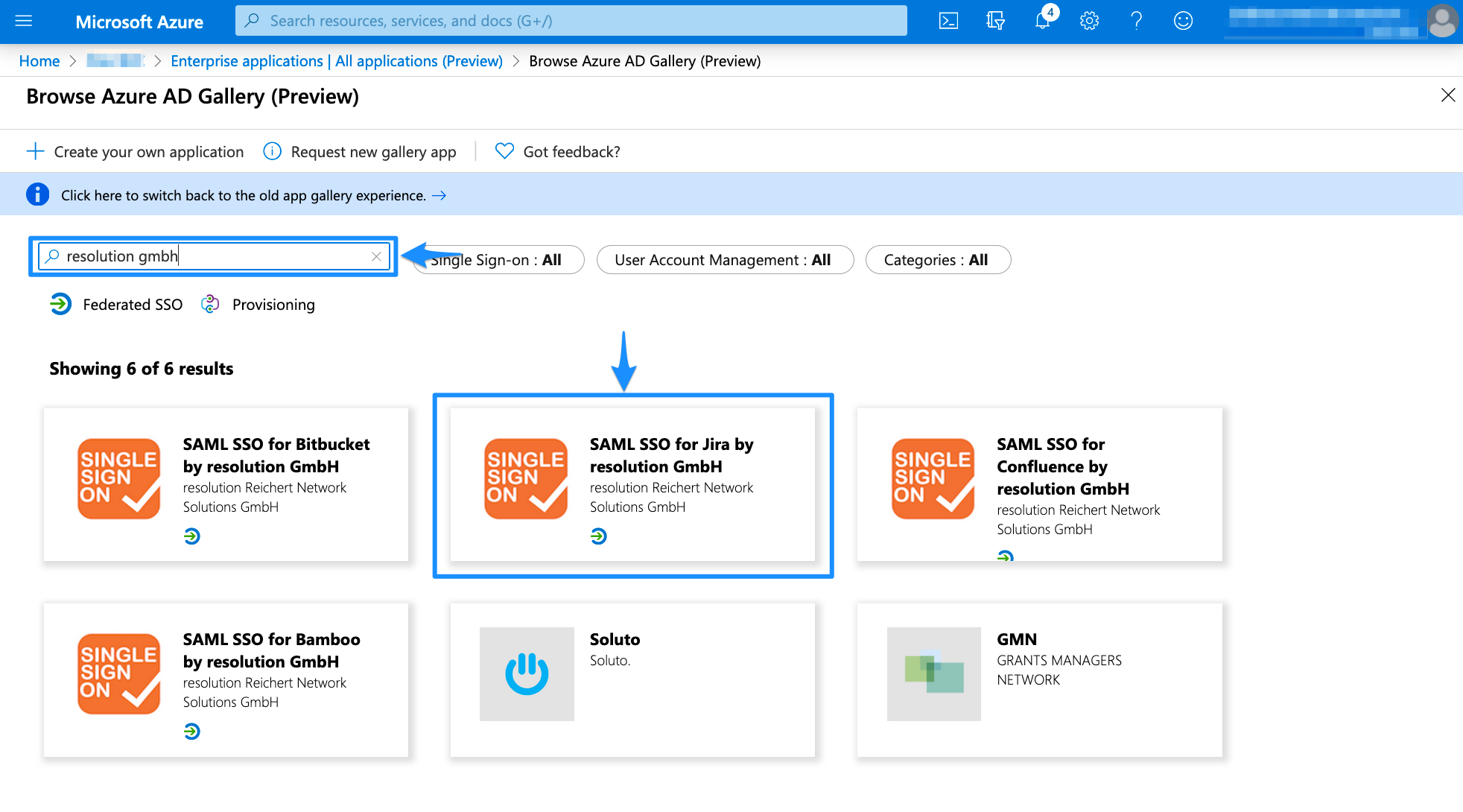
We created presets in the gallery for the SAML SSO app. Search for "resolution gmbh" and choose the version which matches your Atlassian product, e.g. "SAML SSO for Jira by resolution GmbH" for Jira.
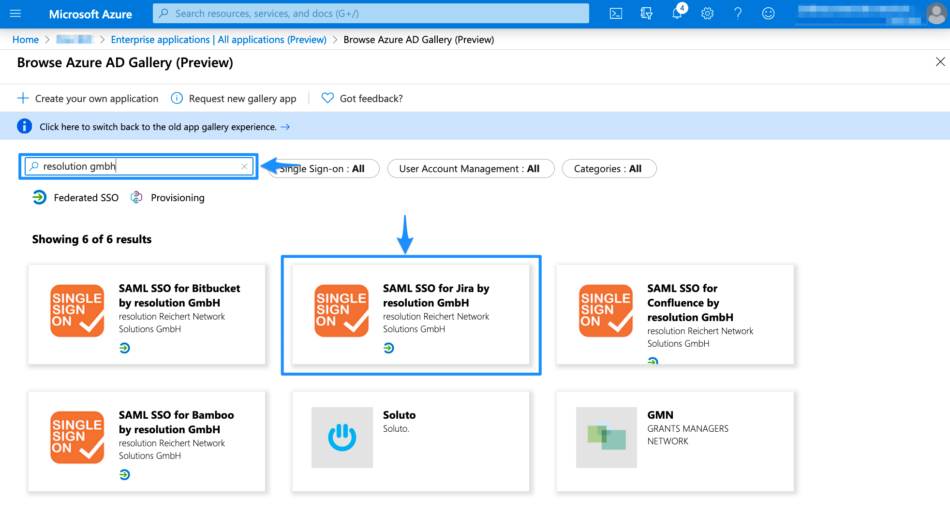 Browse Apps
Browse AppsClick Add to add a new enterprise application. You can also choose a new name for it.
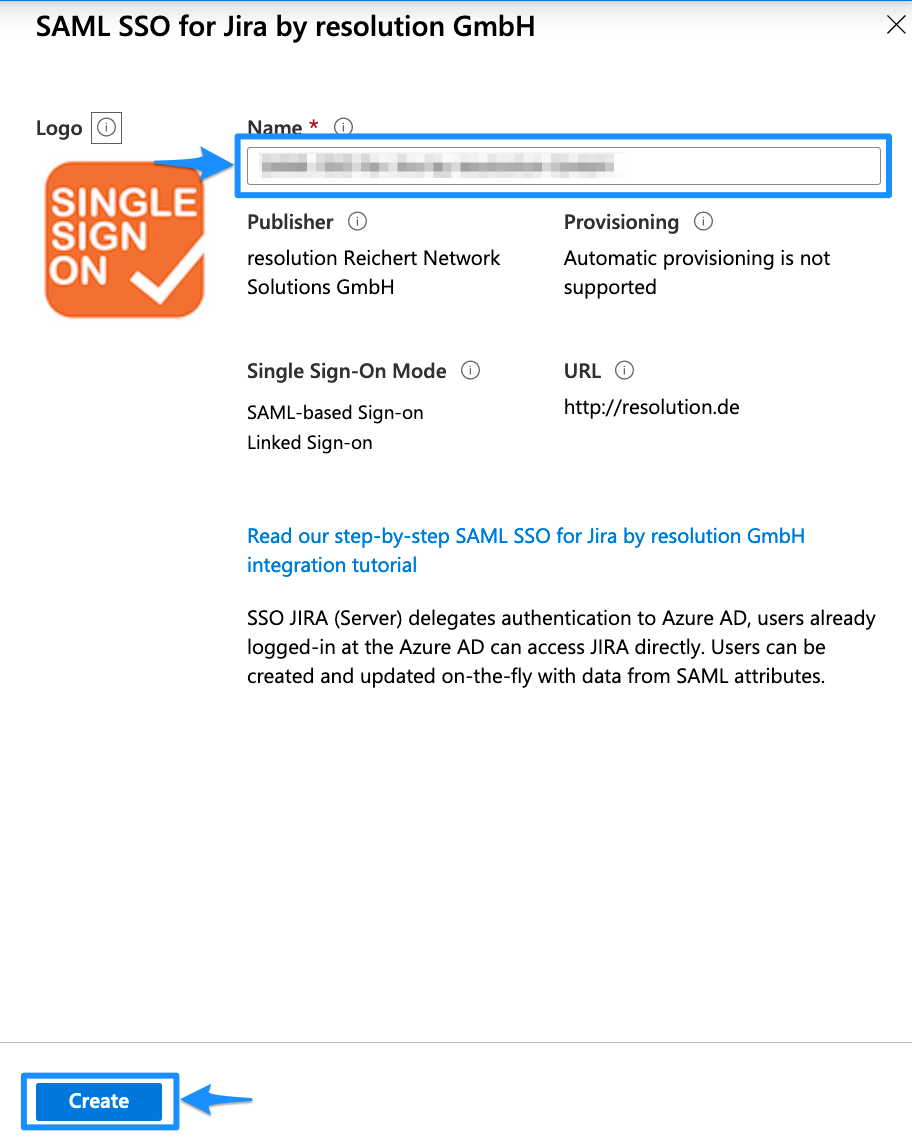
Please wait until the Azure portal redirects you to the enterprise application you just created. This can take a couple of seconds. For the next steps, you will configure the enterprise application.
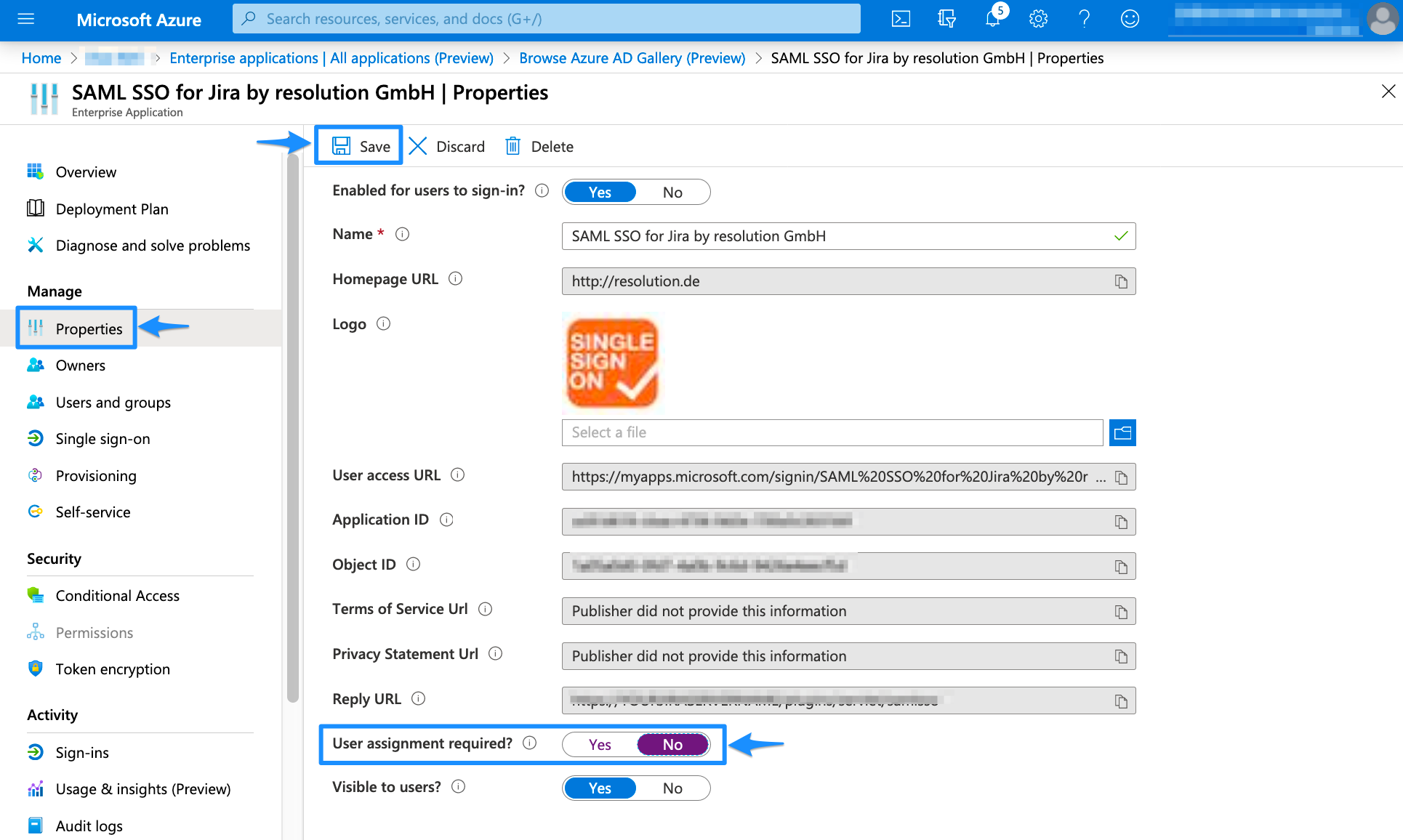
Deactivate User Assignment Required
In the left panel, click Properties. In the new window, scroll down to User assignment required? and set the option to NO. Afterward, Save your configuration.
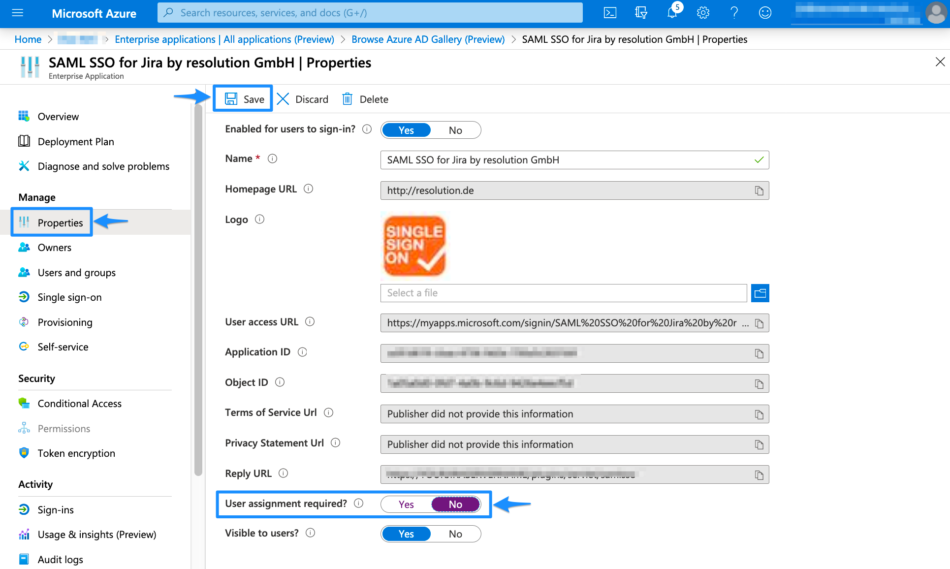 Deactivate User Assignment Required
Deactivate User Assignment Required
Configure the SSO
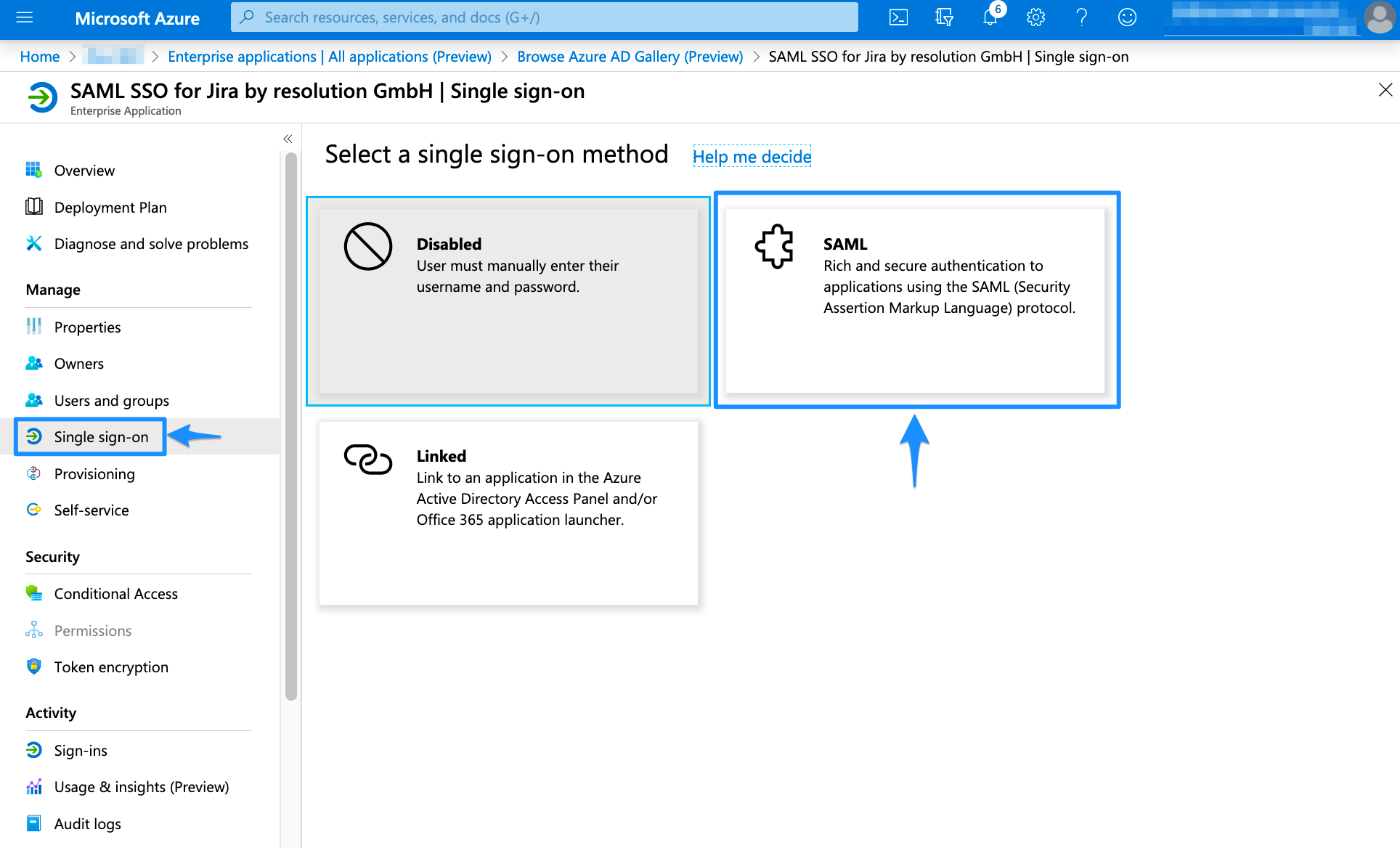
In the left panel under Manage, choose "Single sign-on". Then click SAML for the Single Sign On method.
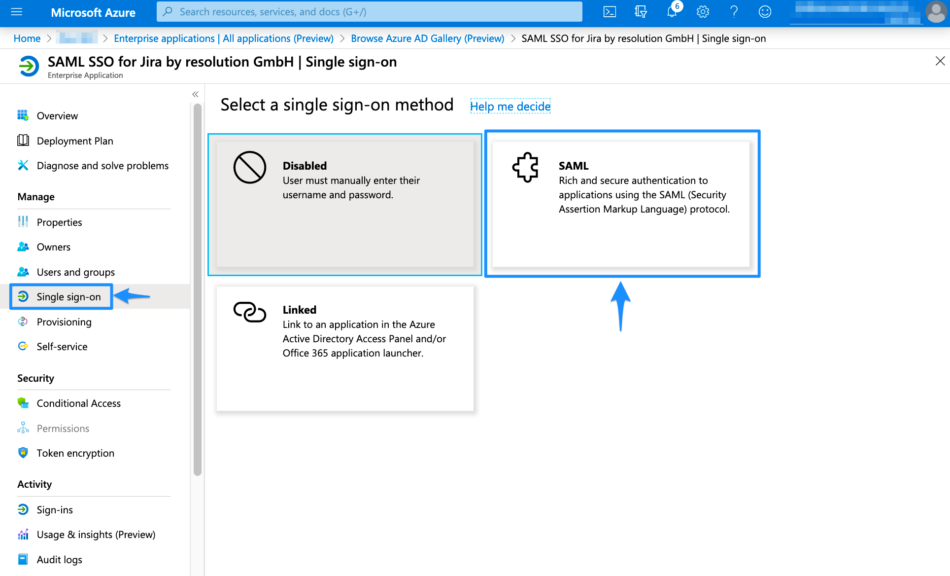
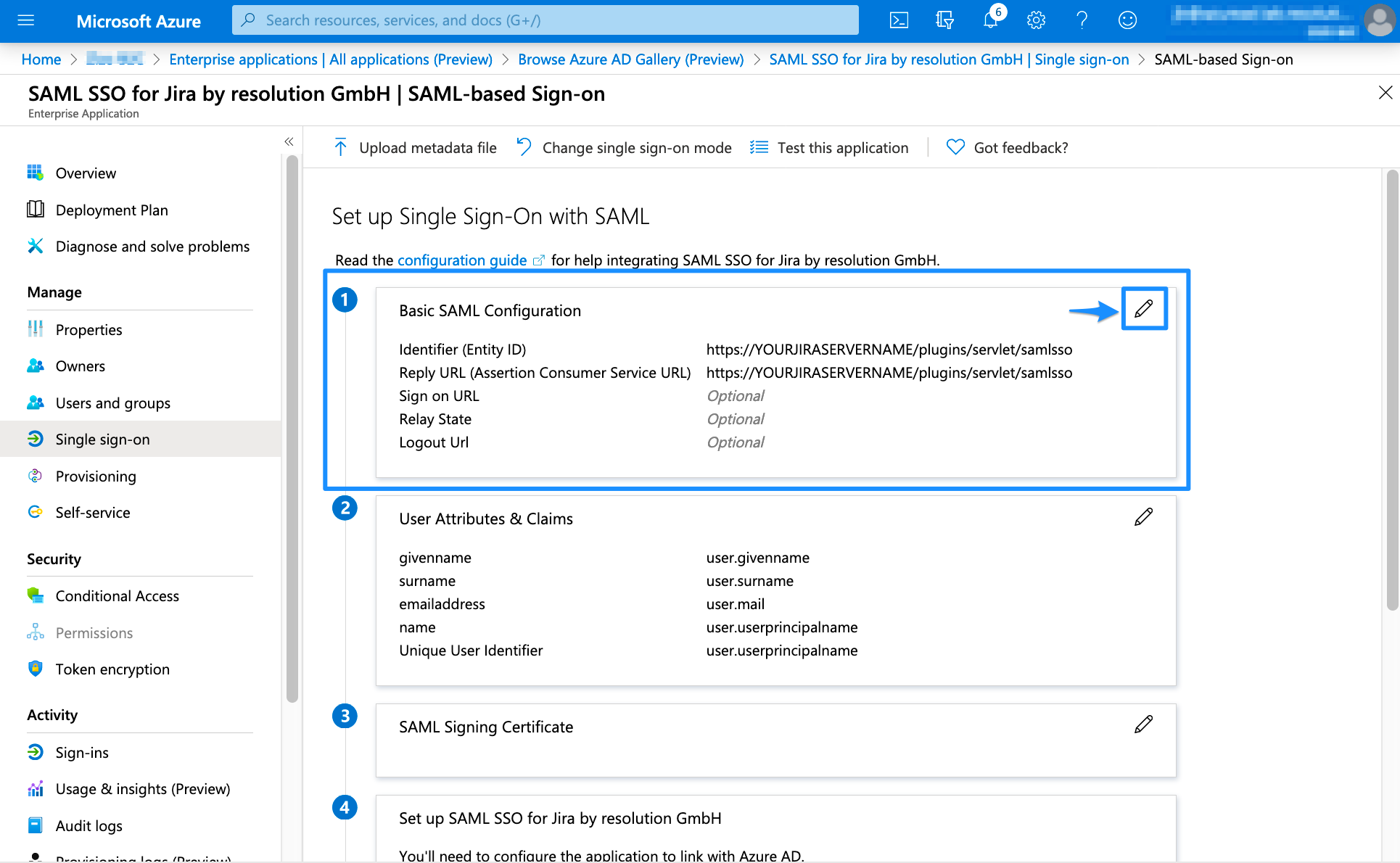
Click the pen symbol in Basic SAML Configuration.
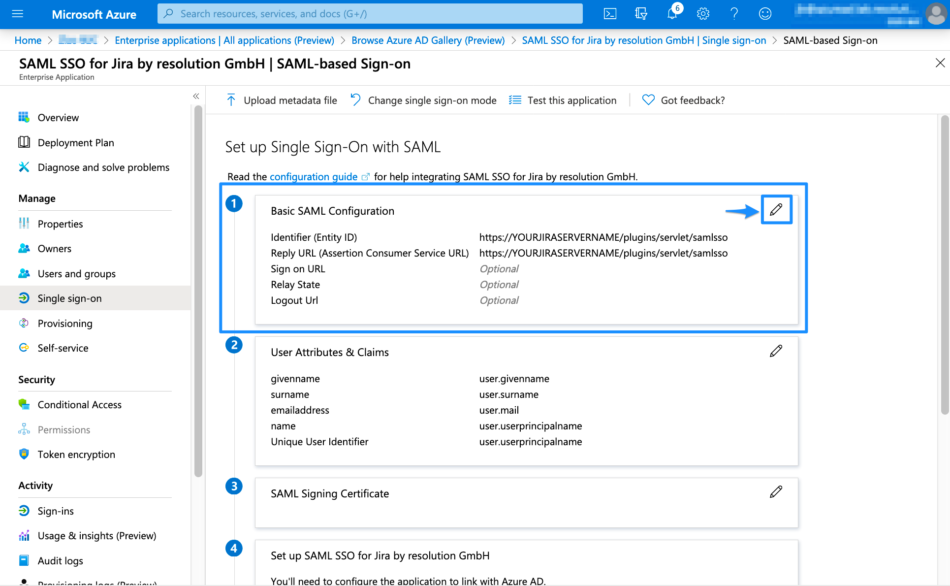
Set the Identifier (Entity ID) and the Reply URL (Assertion Consumer Service URL). You can find both in the last window of the wizard.
In general, the needed URL for both is: https://<base-url>/plugins/servlet/samlsso
You need to substitute <base-url> with the base URL of your Atlassian product instance. The gallery application already provides the needed URLs. You only have to substitute YOURJIRASERVERNAME with the URL of your Atlassian product instance and then click Save.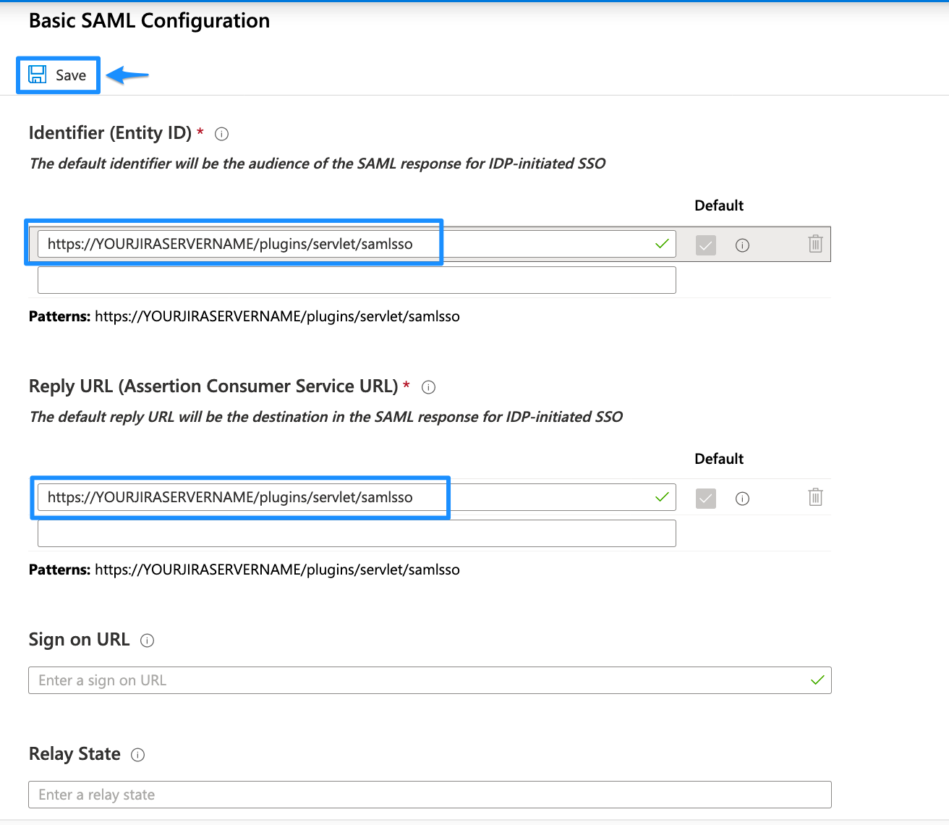 SAML SSO Basic Configuration URLs
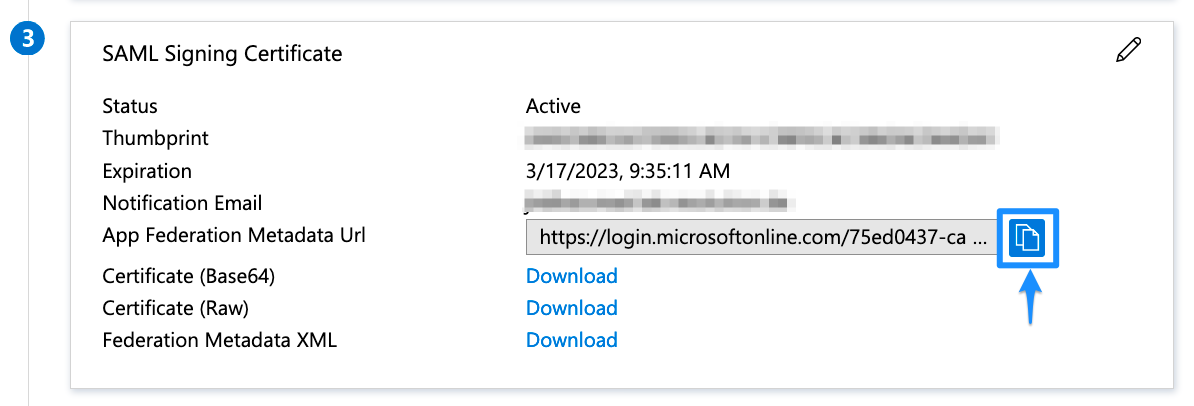
SAML SSO Basic Configuration URLsScroll down to SAML Signing Certificate and copy the App Federation Metadata Url. The link will be used to configure the SAML SSO app.
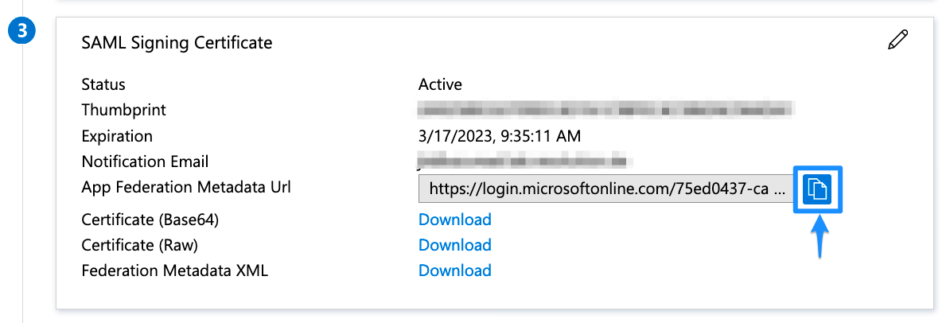
The configuration in Azure AD B2C is now finished. In the next step, we will finish the configuration in the SAML SSO wizard.
Finishing the Configuration - Wizard
Paste the App Federation Metadata Url that was obtained before in the "Metadata URL" textfield.
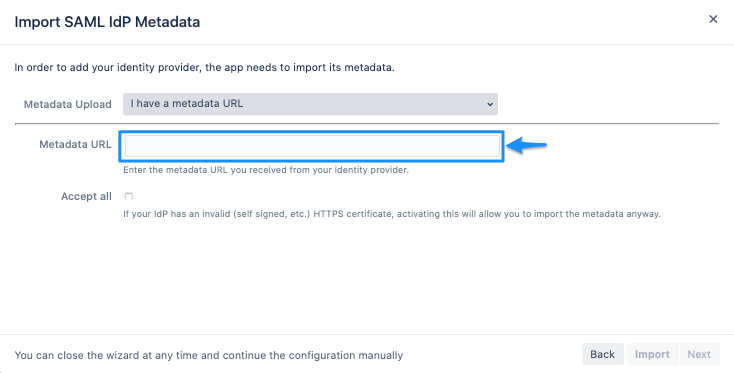 Metadata URL
Metadata URLClick on "Import".
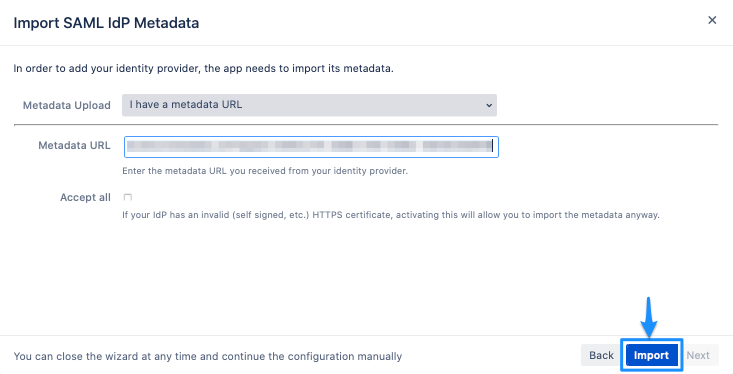
Click on "Next" to continue.
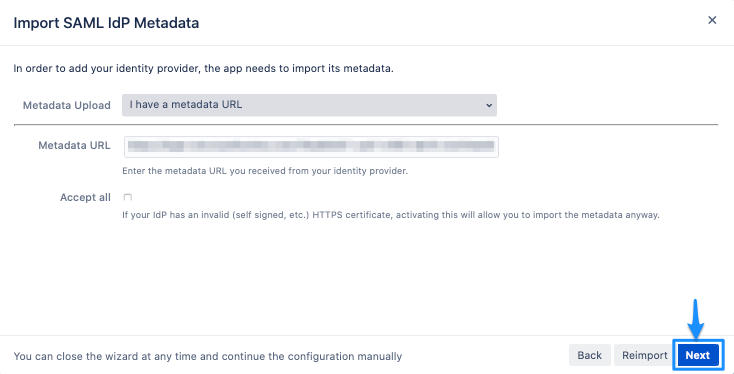
For User update, choose Update from SAML-Attributes.
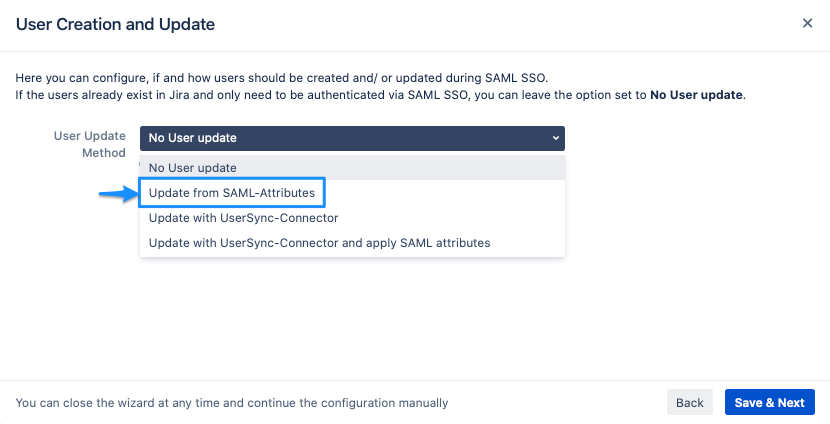
The window now expands. There are various options you can set. For this tutorial, new users should be created automatically when first accessing your Atlassian product instance, thus tick "Create New Users".
You can also choose the directory for new users or to update non-SAML provisioned users, i.e. which are already present in your Atlassian product. By activating the option, they can also be updated via SAML attributes when they log in.
Further, the "Full Name Attribute" and "Email Attribute" must be set.
Set the Full Name Attribute to http://schemas.microsoft.com/identity/claims/displayname
and the Email Attribute to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name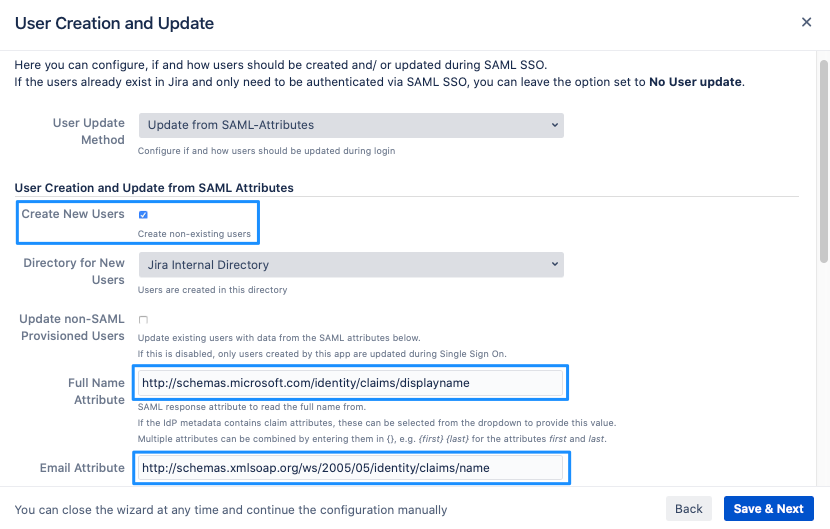 User Attributes
User AttributesScroll down to the group settings.
Depending on your Atlassian product, it is a good idea to set (default) user group(s) for new users, such as jira-servicedesk-users for Jira SD, confluence-users for Confluence or stash-users for Bitbucket. Without assigning new users to the product specific group, they are not able to use your Atlassian product. Also, feel free to activate any option which suits your needs.
Click on Save & Next.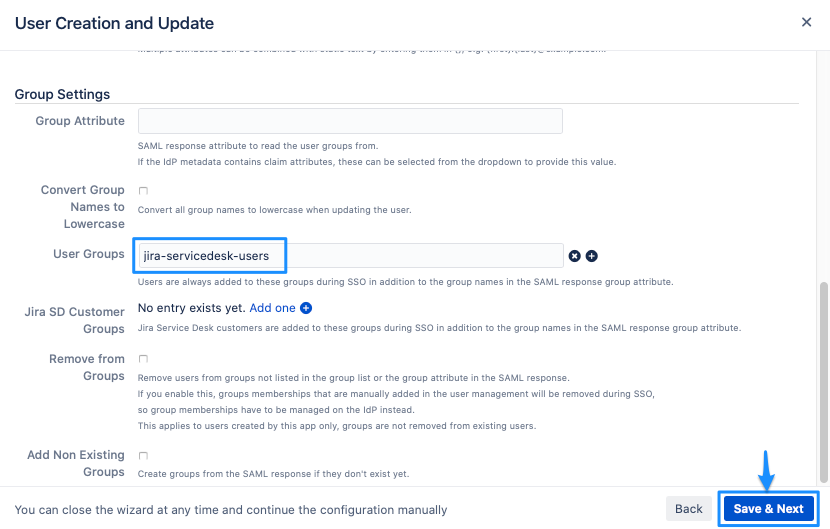
Testing SSO
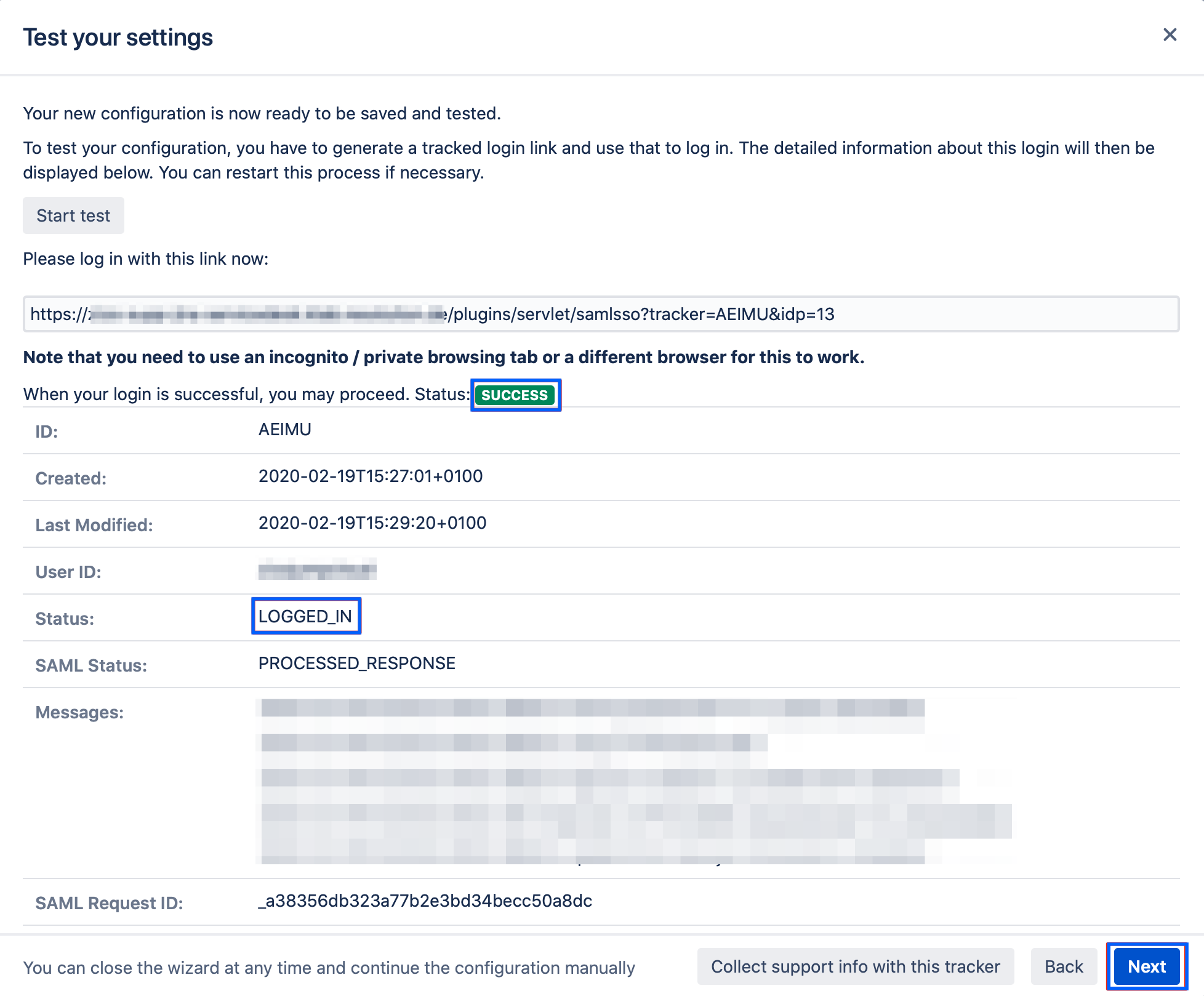
The wizard also allows testing the Single Sign On. Just follow the steps to test if the login works as expected.
Click on "Start test" to proceed.
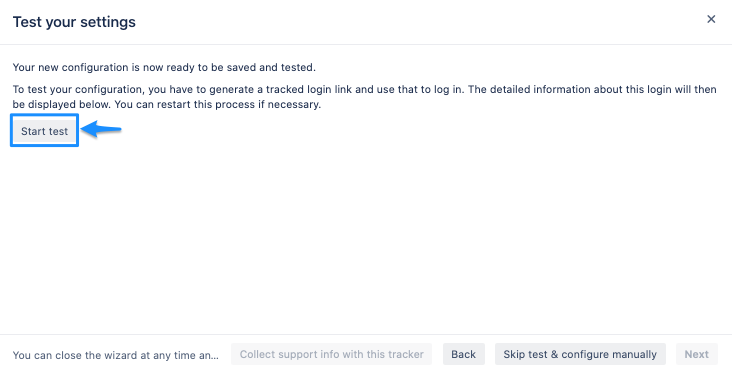
Copy the blue marked link and open a new incognito/private tab or a different web browser. Then, paste the link and navigate to it.
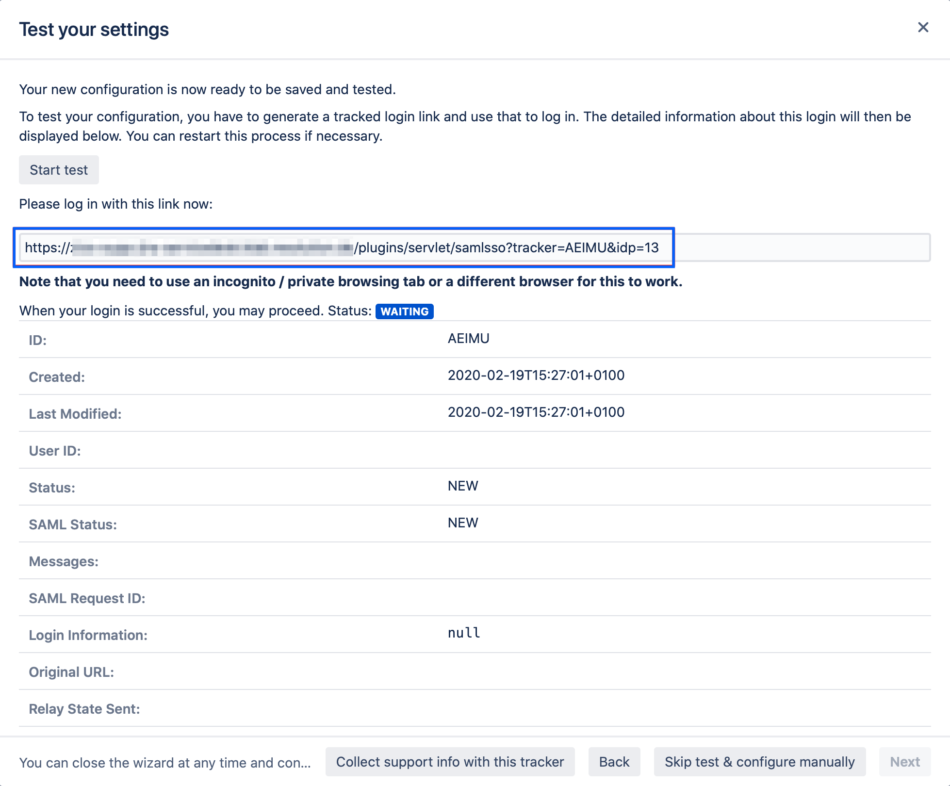
You will be now redirected to Azure AD's login page. Please log-in with your username and password.
If everything worked fine, you will be logged in to your Atlassian product. In the other tab/browser in which you were configuring the SAML SSO plugin, you can see also the "SUCCESS" status, if everything worked as expected.
Click Next to proceed.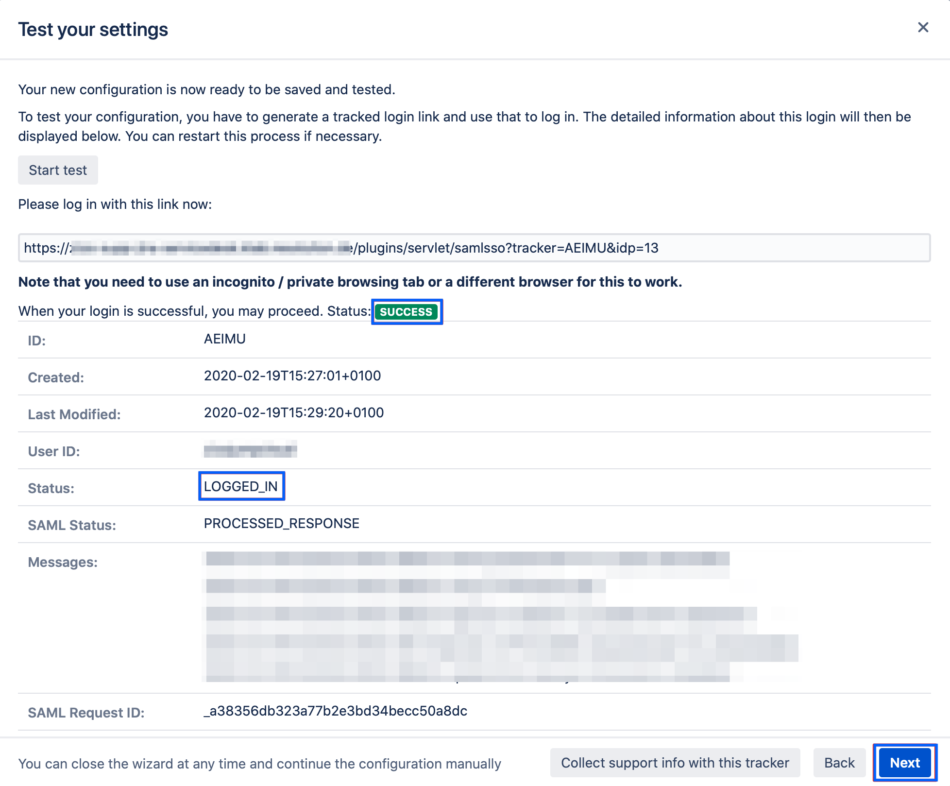
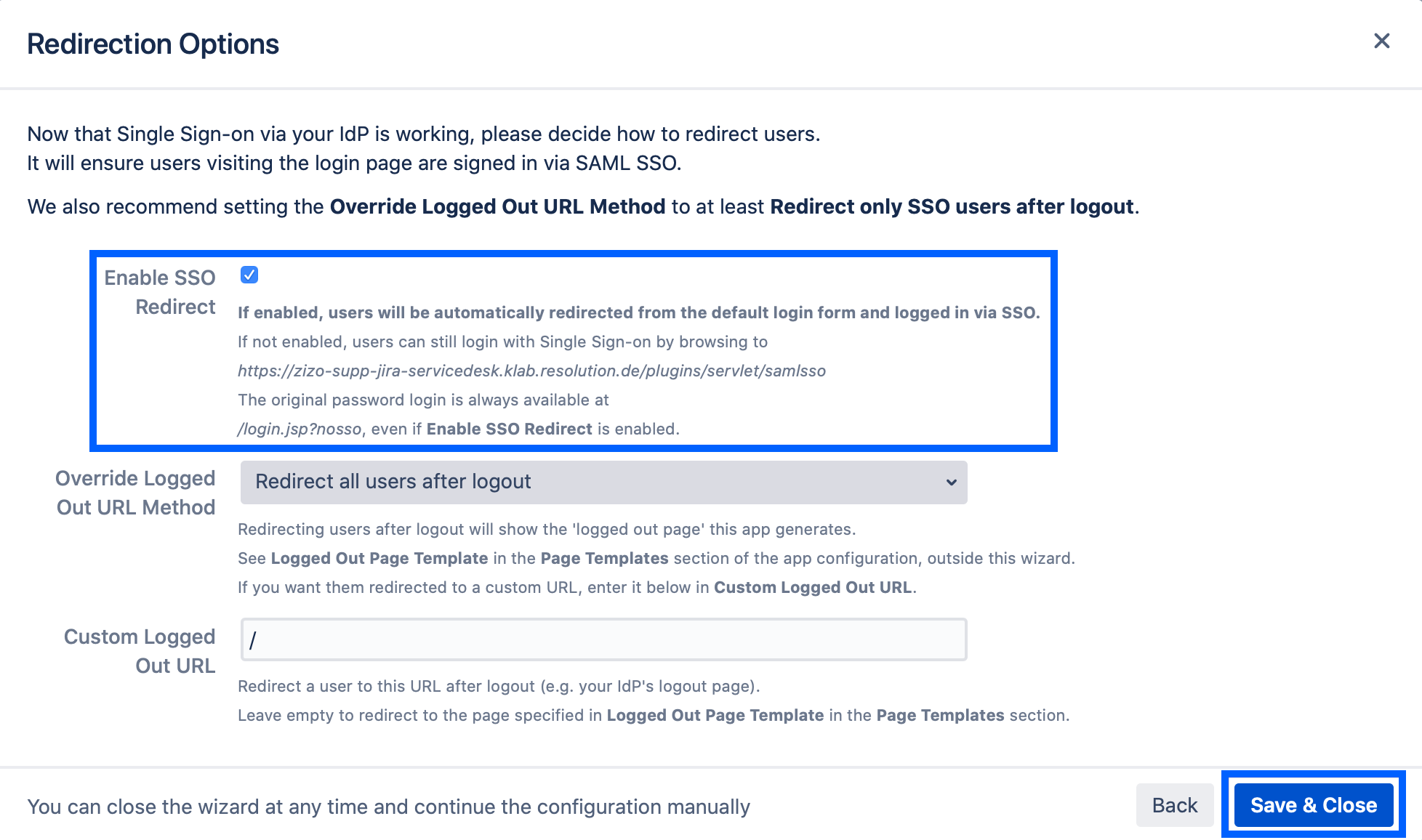
SSO Redirection
As a last step, you can set the Enable SSO Redirect option. If set, all users will be redirected to Single Sign On, thus they will be logged in via the IdP.
Click on Save & Close to finish the configuration.